TRUST TALKS: VIDEO SERIES ON CYBER & TELECOMS SECURITY!
The Mobile Network Battlefield
SECURITY NEWS
AdaptiveMobile Security integration with Enea, GLOMO Awards & ROCCO Recognition
In light of the acquisition of AdaptiveMobile Security by Enea back in July, in this next episode of TrustTalks we will be revealing details on the company’s integration with Enea as well as the ample scope to leverage product synergies between Enea’s business units. We will also be discussing AdaptiveMobile Security’s win for Best Authentication and Security Solution for Mobile Networks at the GLOMO Awards, as well as the recent ROCCO Tier 1 signalling firewall recognition the company obtained.

TOPIC OF THE DAY
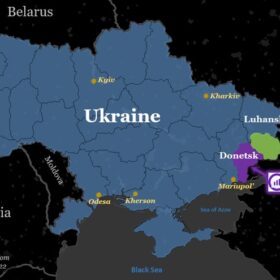
The Mobile Network Battlefield in Ukraine

WHAT’S GOING ON OUT THERE?
STIR/SHAKEN and Pegasus Spyware

FAQ
From our extensive global experience, we believe to properly secure the national critical communications infrastructure of any country requires a multi-layered approach. Collaboration is essential between private and public sector bodies (national regulators, mobile operators and governments) in the development of effective, consistently applied security measures. This includes the sharing of threat-related intelligence and facilitating the development of cross-sector practices in securing any nation’s key communications assets and infrastructure.
Attackers can target core network vulnerabilities to attain and further amplify advantage in offensive military operations. The form that cyber network attacks can take varies, but at a high level the following are possible:
-Surveillance/location tracking
-Message/Call/Data Interception
-Fraud (against the operator or the subscriber)
-Phishing* (malware delivery)
-Denial of Service
-Information harvesting
TrustTalks telco security series is an initiative of the company Enea AdaptiveMobile Security. This video series is intended to serve as an informative and educational channel for telecom companies, regulators, and CPaaS providers. A series of videos hosted by the renowned security analyst Patrick Donegan and with the participation of a panel of security experts, who will discuss the most relevant cyber security issues and share key security insights.